proton mail
Two-factor authentication.
Send password protected messages to anyone.
Import a CSV contact list.
Search capabilities are limited.
The web interface is sometimes slow.
Integration with other email clients is cumbersome.
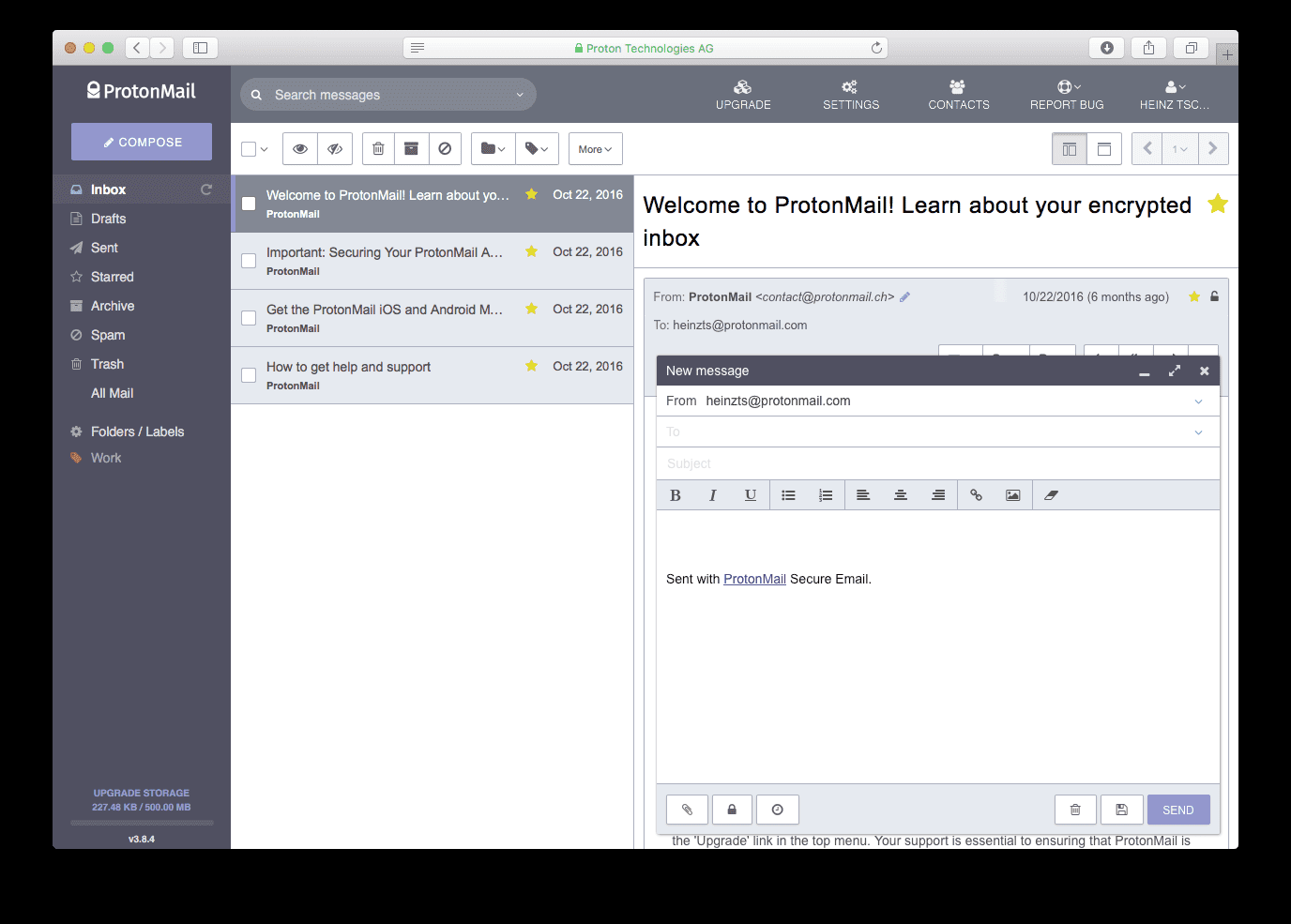
ProtonMail is a free, open source, encrypted email provider based in Switzerland. It works on any computer via the ProtonMail website and Android and iOS mobile apps.
When talking about any encrypted email service, the most important feature is whether others can access your messages, and with ProtonMail, the answer is yes because it features end-to-end encryption.
Without your unique password, no one can decrypt ProtonMail messages, not even ProtonMail employees, its ISP, your ISP, or the government.
ProtonMail is so secure that it cannot recover your email if you forget your password. Decryption occurs when you are logged in, which means the service cannot decrypt emails without your password or recovery account on file.
ProtonMail also does not retain your IP address information. With a no-log email service like ProtonMail, emails can't be traced back to you.
The free version of ProtonMail supports 1GB of email storage and usage is limited to 150 emails per day.
Purchase the Plus or Unlimited service to get more email storage, email aliases, priority support, labels, custom filtering options, auto-responder functionality, built-in VPN protection, and the ability to send more emails every day. Business plans are also available for organizations to use.
02 out of 05silent mail
Supports IMAP and POP.
Optional two-step verification.
Import contacts from CSV file.
Spam filters and autoresponders.
Includes 10 GB of storage.
There is no free trial.
Available for iOS only.
Can be expensive.
Hushmail is an encrypted email service that has been around since 1999. It uses state-of-the-art encryption methods to keep emails secure and locked. Not even Hushmail can read your messages; only someone who knows your password can do this.
This service allows you to send encrypted messages to Hushmail users as well as non-users who have Gmail, Outlook Mail, or other similar email client accounts.
The web version of Hushmail is easy to use and provides a modern interface for sending and receiving encrypted messages from any computer.
When you create a new Hushmail account, choose from a variety of domains to use in your address, such as @hushmail.com or @hush.com.
There are several personal and business options when signing up for Hushmail, but none of them are free.
03 out of 05Anti-mail
Supports IMAP.
No IP address logs are kept.
Includes Safebox, a built-in password manager.
Unable to send encrypted email to non-users.
Storage space is limited.
10-day free trial only.
If you're concerned about email privacy, CounterMail provides a secure implementation of OpenPGP-encrypted email in your browser. Only encrypted emails are stored on CounterMail servers.
Additionally, the server (located in Sweden) does not store emails on the hard drive. All data is stored on CD-ROM only. This approach helps prevent data leaks, where data is likely to be lost when someone attempts to directly tamper with the server.
With CounterMail, you can also set up a USB drive to further encrypt emails. The decryption key is stored on the device and is also required to log into your account. This way, even if a hacker steals your password, they can't decrypt it.
The added physical security of a USB device makes using CounterMail less simple and convenient than other secure email services, but you do get IMAP and SMTP access, and you can use it with any OpenPGP-enabled email program, such as K- 9Mail Android.
After the 10-day free trial, purchase a plan to continue using the service. Trial version includes 100 MB of space.
04 out of 05Tutano Tower
Apps available for iOS and Android.
Includes 1 GB of storage.
Open source.
Support spam filtering.
Alias addresses are only available for paid accounts.
IMAP is not supported.
Unable to import contacts in batches.
Tutanota is similar to ProtonMail in design and security level. All Tutanota emails are encrypted from sender to recipient and decrypted on the device. No one else can access the private encryption key.
Simply use this email account to exchange secure emails with other Tutanota users. For encrypted emails outside the system, specify the password that recipients will use when viewing the message in a browser. The interface also allows them to reply securely.
The web interface is user-friendly and there is a search function so you can search for previous emails.
Tutanota uses AES and RSA for email encryption. The servers are located in Germany, which means German regulations apply.
Free accounts can create email accounts using Tutanota domains, while paid plans can create custom domains. Tutanota domains include: @tutanota.com, @tutanota.de, @tutamail.com, @tuta.io and @keemail.me.
Some features in this service are only available on paid plans. For example, the Revolutionary edition offers 15 aliases, while the Legend plan expands storage to 500 GB.
05 out of 05mail fence
Digital email signature proves authorship.
Supports two-factor authentication.
Includes spam blocker.
Import contacts from Outlook, CSV files, Gmail, and more.
Calendar and file storage for documents.
Limited online storage space.
An alternate email address is required as an activation key.
The private key is stored on the Mailfence server.
Mailfence is a security-focused email service that features end-to-end encryption to ensure that no one but you and your intended recipients can read your messages.
The service includes an email address and a web interface that includes OpenPGP public key encryption. Create key pairs for your accounts and manage key storage for the people you want to email securely.
This OpenPGP standardization means you can access Mailfence through your email program of choice using IMAP and SMTP as well as secure SSL/TLS connections. You cannot use Mailfence to send encrypted messages to someone who does not use OpenPGP and does not have a public key available.
For online storage, free Mailfence accounts offer 500 MB of space, while paid accounts offer plenty of space and the option to use your own domain name as your Mailfence email address.
Mailfence's software is only available for inspection by moderation teams, academic researchers, and other reputable groups because it is not open source and therefore less secure and private.
Mailfence stores your private encryption key on Mailfence servers, but insists that it cannot be read because it is encrypted with your password (via AES-256) and there is no root key that allows the service to decrypt it using your Key encrypted message.
Mailfence uses servers located in Belgium, so the company can only be forced to reveal private data through a Belgian court order.
If you use an email service that offers end-to-end encryption, you're taking a big step toward keeping your email secure and private. To make life more difficult for hackers, here are some precautions:
- Beware of keylogging software that records what you type on your keyboard. These programs can prevent encryption if all a hacker needs to access an account is the password.
- Never leave your mobile device or computer unattended. Additionally, make sure the device is protected with a strong password or biometrics and does not allow guest accounts or similar unprotected access. If supported, you can also add two-factor authentication.
- Be wary of social engineering. Phishing attempts are typically conducted via email, instant messaging, VoIP, or social network messages and can be designed or customized specifically for you. These communications are a ploy to trick you into providing personal details such as passwords and banking information.
- Don't write down or share passwords. Never write down your passwords unless they are stored in a secure password manager.
