what to know
- The HKLM registry hive stores software and hardware information for Windows.
- Run the regedit command to open the Registry Editor. Look for HKEY_LOCAL_MACHINE on the left.
- This registry hive is more like a shortcut, so you cannot create new keys in it.
This article explains the purpose of this registry hive and what is stored inside, as well as how to find it in Registry Editor.
HKEY_LOCAL_MACHINE, often abbreviated as HKLM , is one of several registry hives that make up the Windows registry. This specific hive contains the software you have installed as well as most of the configuration information for the Windows operating system itself.
In addition to software configuration data, this hive contains a lot of valuable information about currently detected hardware and device drivers.
In Windows 11, Windows 10, Windows 8, Windows 7, and Windows Vista, information about your computer's startup configuration is also included here.
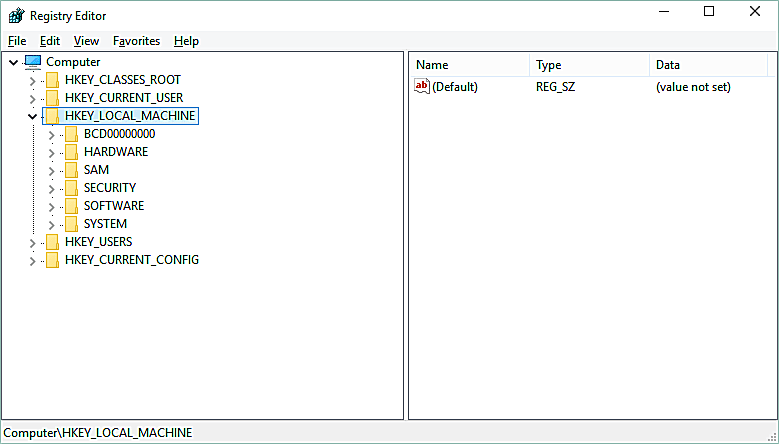
As a registry hive, HKEY_LOCAL_MACHINE can be easily found and opened using the Registry Editor tool included with all versions of Windows:
Open the Registry Editor. Executing the regedit command in the Run box is a quick way to get there.
Find HKEY_LOCAL_MACHINE on the left side of the Registry Editor.
If you or someone else has used Registry Editor on your computer before, you may need to collapse any open registry keys until you find the hive. Using the left arrow key will collapse whatever is currently selected.
Double-click or double-click HKEY_LOCAL_MACHINE to expand the hive, or use the small arrow on the left.
The following registry keys are located under the HKEY_LOCAL_MACHINE hive:
- HKEY_LOCAL_MACHINEBCD00000000
- HKEY_LOCAL_MACHINECOMPONENTS
- HKEY_LOCAL_MACHINEDRIVERS
- HKEY_LOCAL_MACHINEHARDWARE
- HKEY_LOCAL_MACHINESAM
- HKEY_LOCAL_MACHINE schema
- HKEY_LOCAL_MACHINESECURITY
- HKEY_LOCAL_MACHINESOFTWARE
- HKEY_LOCAL_MACHINESYSTEM
The keys under this hive on your computer may vary depending on your version of Windows and your specific computer configuration. For example, newer versions of Windows do not include the COMPONENTS key.
The HARDWARE subkey holds data related to the BIOS, processor, and other hardware devices. For example, in Hardware it is Description > System > BIOS where you can find the current BIOS version and vendor.
The SOFTWARE subkey is the most frequently accessed subkey in the HKLM hive. It is organized alphabetically by the software vendor, and is where each program writes data to the registry so that the next time you open the application, its specific settings can be automatically applied so you don't have to re-install it every time you use the program. Configurator. It is also useful when looking up a user's SID.
The SOFTWARE subkey also contains a Windows subkey (describing various UI details of the operating system), a Classes subkey (detailing which programs are associated with which file extensions), etc.
HKLMSOFTWAREWow6432Node is found on 64-bit versions of Windows, but is used by 32-bit applications. It is equivalent to HKLMSOFTWARE, but not identical as it is separate and its sole purpose is to provide information for 32-bit applications on 64-bit operating systems. WoW64 displays the key for 32-bit applications as "HKLMSOFTWARE".
In most configurations, the following keys are hidden and therefore cannot be browsed like other keys under the HKLM registry hive:
- HKEY_LOCAL_MACHINESAM
- HKEY_LOCAL_MACHINESECURITY
Most of the time, these items appear blank when you open them and/or contain blank subkeys.
The SAM subkey refers to information about the domain's Security Accounts Manager (SAM) database. Within each database are group aliases, users, guest accounts, and administrator accounts, as well as the names used to log into the domain, cryptographic hashes of each user's password, and more.
The SECURITY subkey is used to store the current user's security policy. It links to the security database of the domain in which the user is logged in, or to the registry hive on the local computer if the user is logged in to the Local System domain.
To view the contents of a SAM or SECURITY key, Registry Editor must be opened using the SYSTEM account, which has greater permissions than any other user, even users with administrator privileges.
After opening the Registry Editor with the appropriate permissions, you can explore the HKEY_LOCAL_MACHINESAM and HKEY_LOCAL_MACHINESECURITY keys like any other key in the hive.
Some freeware utilities, such as Microsoft's PsExec, can open Registry Editor with the appropriate permissions to view these hidden entries.
Interestingly, HKEY_LOCAL_MACHINE doesn't actually exist anywhere on the machine, but is simply a container that displays the actual registry data loaded via subkeys within the hive listed above.
In other words, it's like a shortcut to access many other sources of data about your computer. Because of this non-existent nature, neither you nor any program you install can create additional keys under HKEY_LOCAL_MACHINE.
The hive is global, meaning it is the same no matter which user on the computer views it, unlike registry hives such as HKEY_CURRENT_USER, which are specific to each user who views it when logged in.
Although it is often written as such, HKLM is not really an "official" abbreviation. This is important to understand because in some cases, some programs (even tools provided directly from Microsoft) do not allow you to abbreviate hives in registry paths. If you get an error using "HKLM", use the full path instead and see if that resolves the issue.
